Mandatory MFA for Azure: securing emergency access accounts

About a month ago, Microsoft announced the enforcement of multi-factor authentication (MFA) for all user accounts associated with administrative applications related to Azure. The enforcement begins on October 15th; however, organizations can request additional time to prepare, extending the deadline to March 15th if necessary.
The motivations for this enforcement are clear. Protecting accounts with MFA, especially administrative accounts, significantly enhances the security of your tenant and safeguards your digital identities against the majority of cyber threats. Most Azure administrators are already using some form of MFA, and many are also implementing conditional access policies that can be configured to require MFA for logging into the affected applications. Until now, the best practice has been to define exclusions in your conditional access policies to prevent them from affecting your emergency access accounts—commonly known as break-glass accounts—and to rely solely on a long, complex password. Now, we will also need to implement MFA for these accounts.
A second category of accounts affected by this rollout is service accounts. Many, including myself, still utilize user-based service accounts. To ensure that your services are not disrupted by this enforcement, you will need to migrate your user-based service accounts to workload identities. I will be writing a blog post about this soon.
Scope of the Enforcement
Let’s review what exactly will be affected.
Applications:
- Azure portal
- Microsoft Entra admin center
- Microsoft Intune admin center
- Azure command-line interface (Azure CLI)
- Azure PowerShell
- Azure mobile app
- Infrastructure as Code (IaC) tools
Only the three main websites (Azure portal, Entra, and Intune) will be immediately impacted. For the rest, MFA will begin to be enforced in a second phase starting in early 2025.
Accounts:
- All users who sign in to the applications listed above.
- User-based service accounts used for automation.
- Emergency access accounts.
Not affected:
- End-users of services, applications, or websites hosted on Azure.
- Workload identities (managed identities, service principals).
MFA for Emergency Access Accounts
With emergency access accounts now required to comply with the new MFA requirements, it is recommended to secure these accounts using FIDO2 passkeys or certificate-based authentication. Both of these methods are phishing-resistant options, but I personally prefer FIDO2 and would recommend it for all administrators, especially global administrators.
If you are using FIDO2 passkeys, remember to adjust your conditional access policies to mandate phishing-resistant MFA.
Setting Up Emergency Access Accounts with a FIDO2 Passkey
Create the Accounts
Follow these steps to create an emergency access account. It is advisable to create two of these accounts.
- Navigate to the Microsoft Admin portal (not to Entra, or you will have to reset the password on the first login) to create a new user.
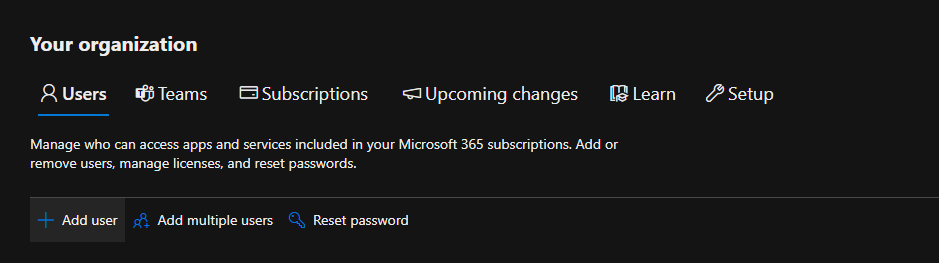
- Fill out the names, username, and password. Choose a meaningful display name. Ensure you uncheck the box that requires this user to change their password upon first sign-in.
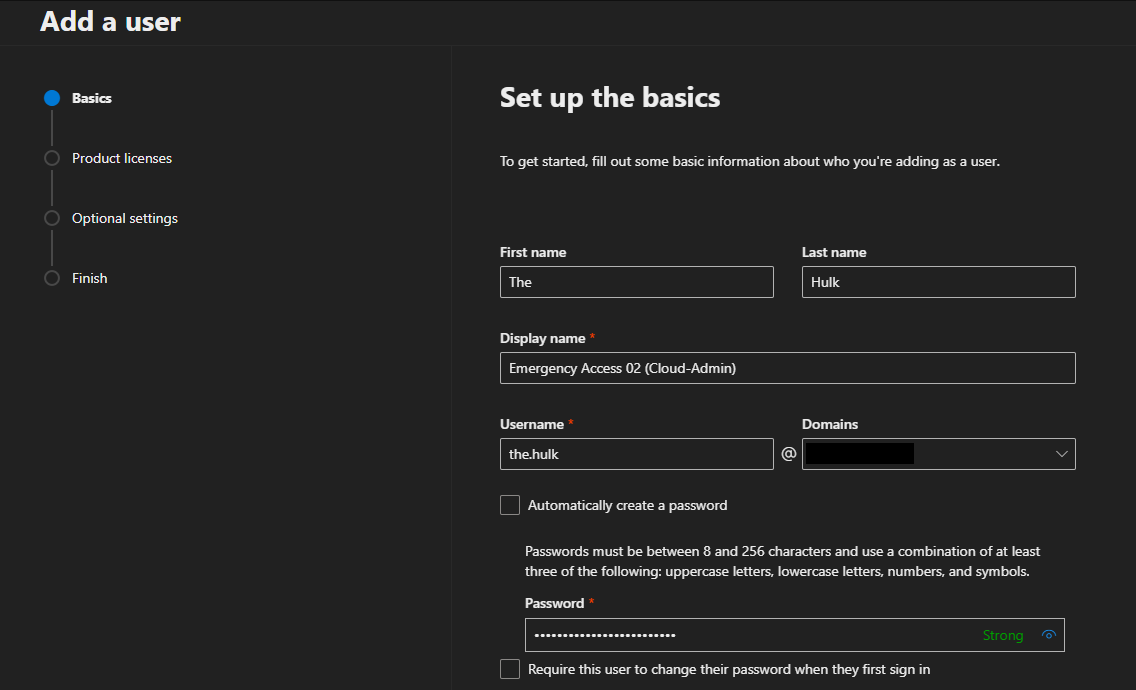
- This user does not need a license.
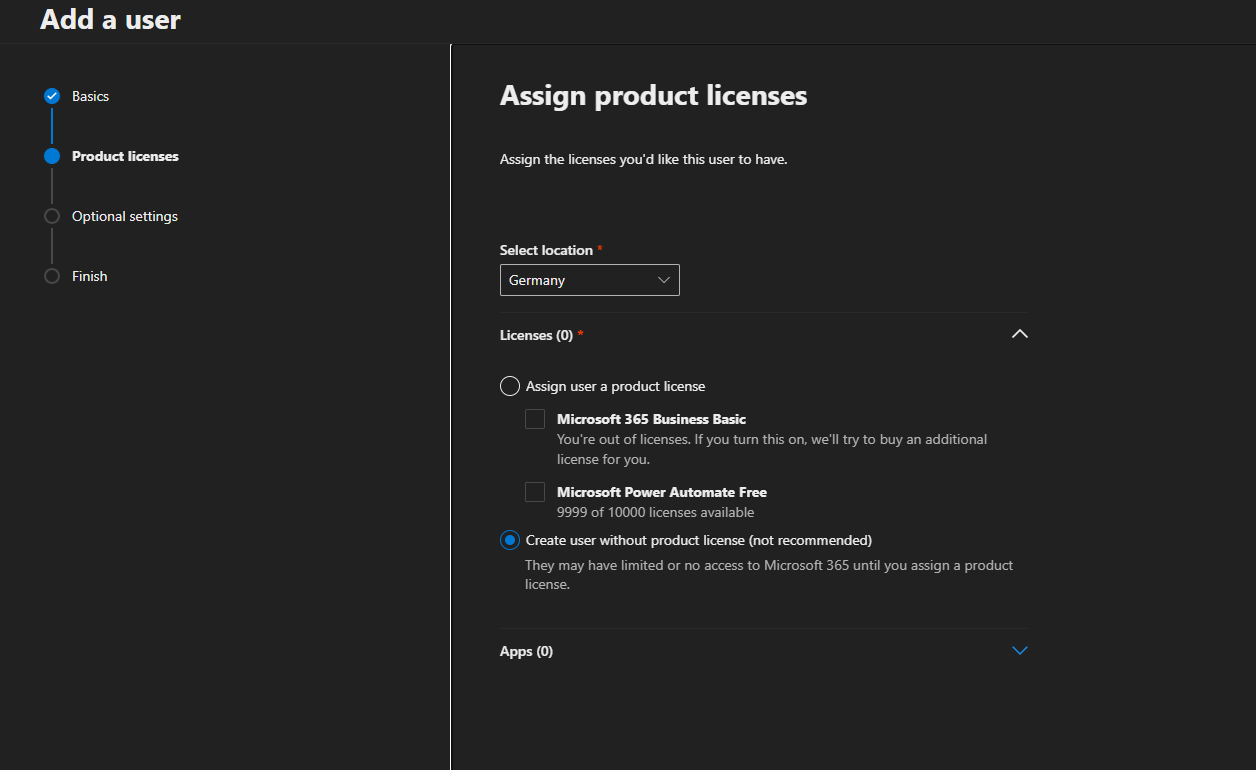
- Assign the Global Administrator role.
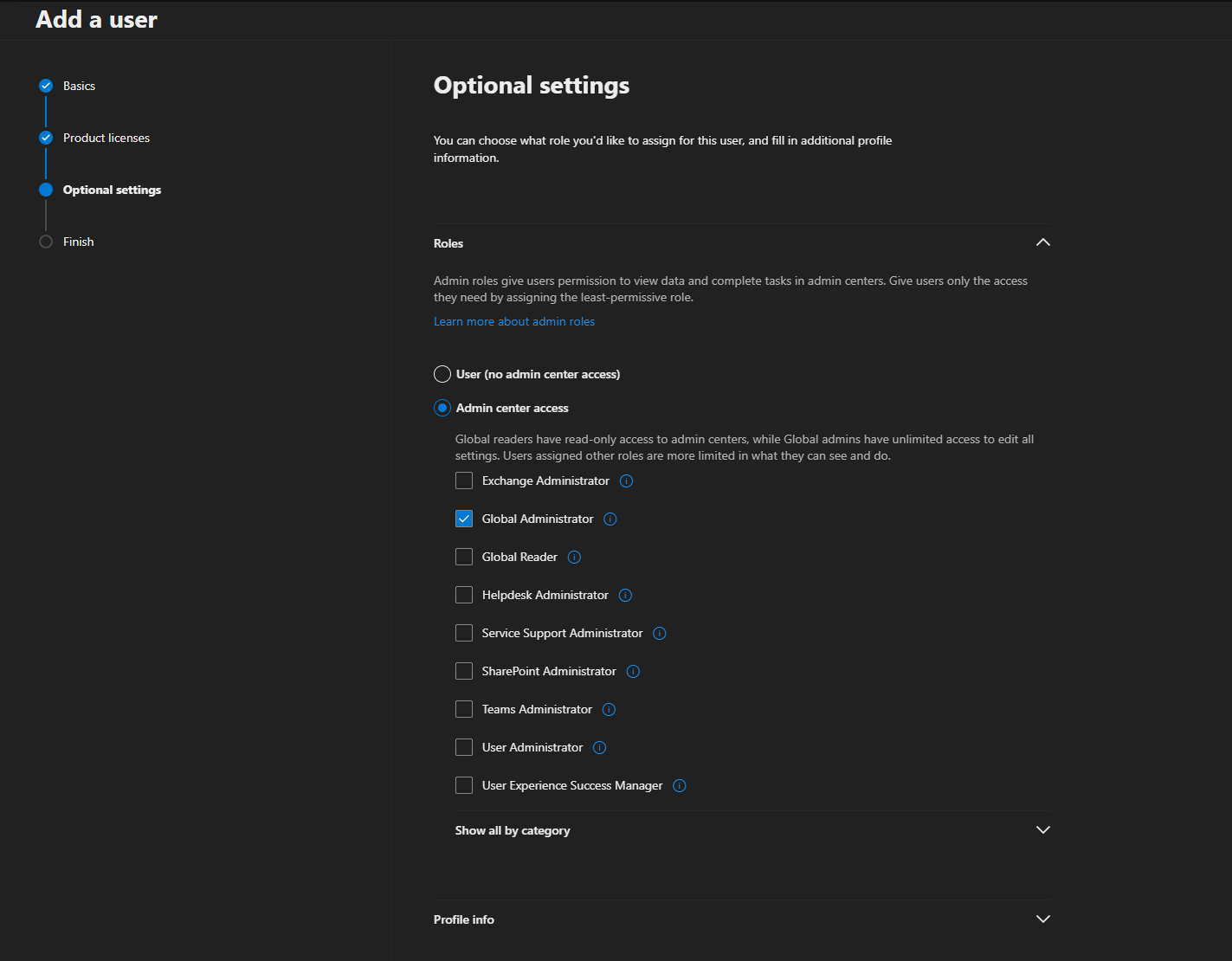
- Complete the wizard.
Activate FIDO2 and Temporary Access Pass
The main idea is to use a temporary access pass to log in as the emergency access account and register the FIDO2 passkey.
- Create a group that includes all your emergency access accounts. If you haven’t done so already, this group will be used to exclude these users from any conditional access policies, as well as to simplify management.
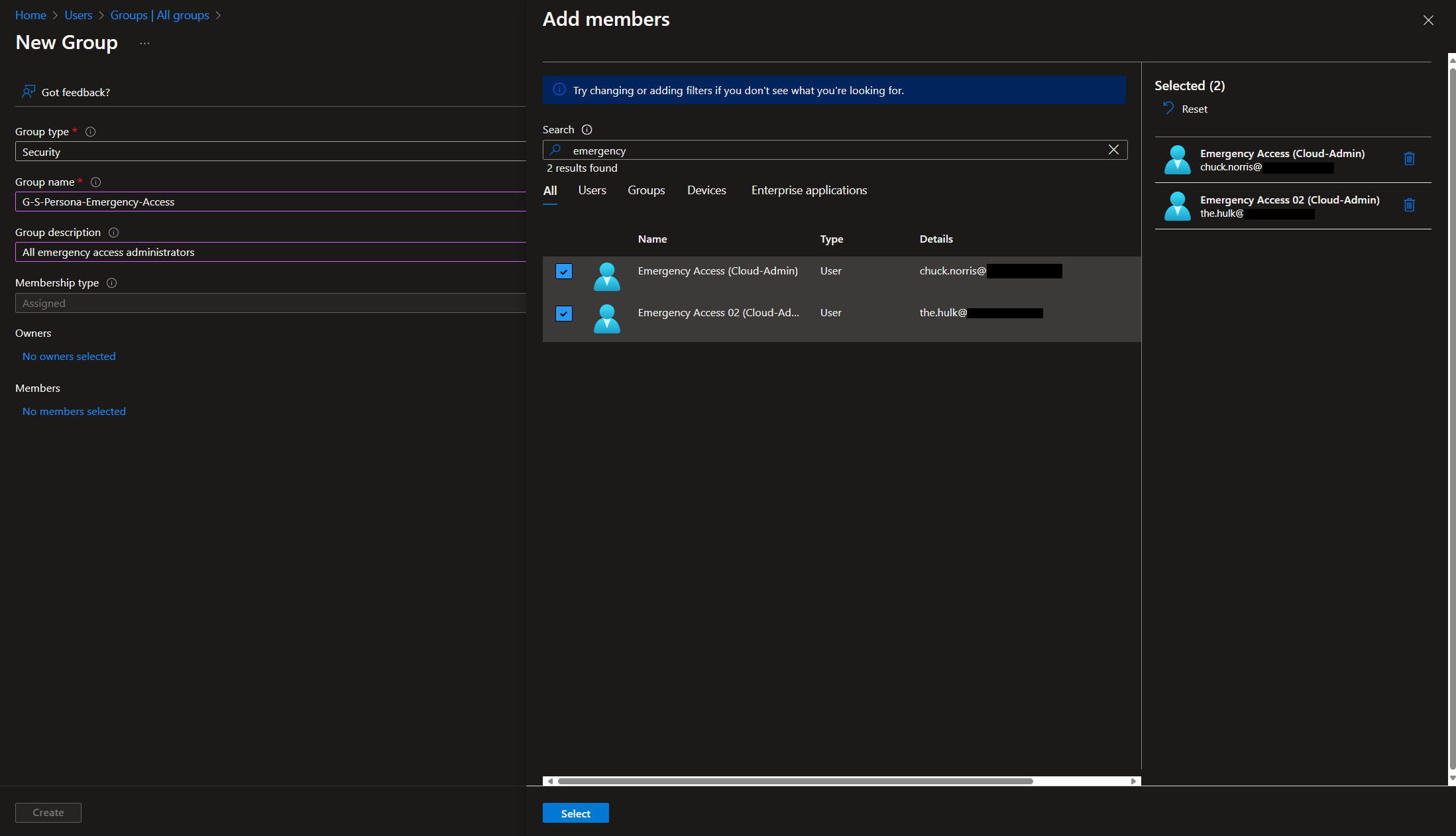
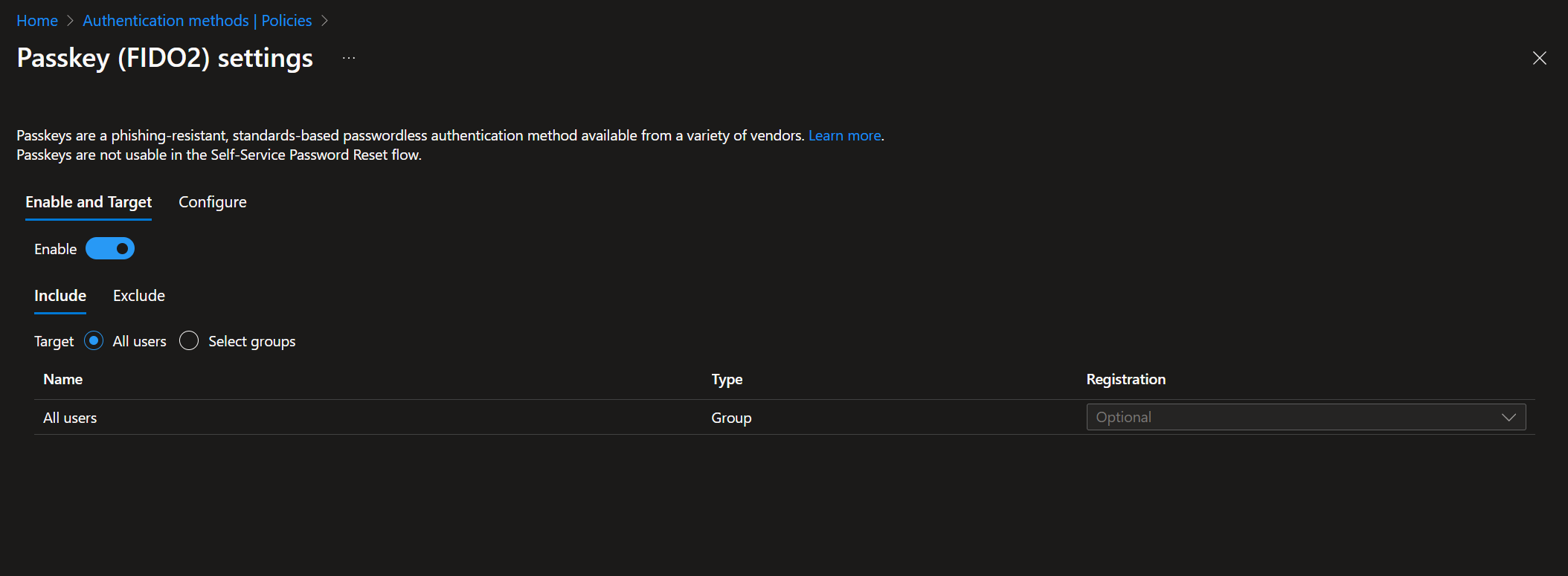
- Navigate to the Authentication Policies and enable FIDO for all users, as well as the Temporary Access Pass for the newly created group.
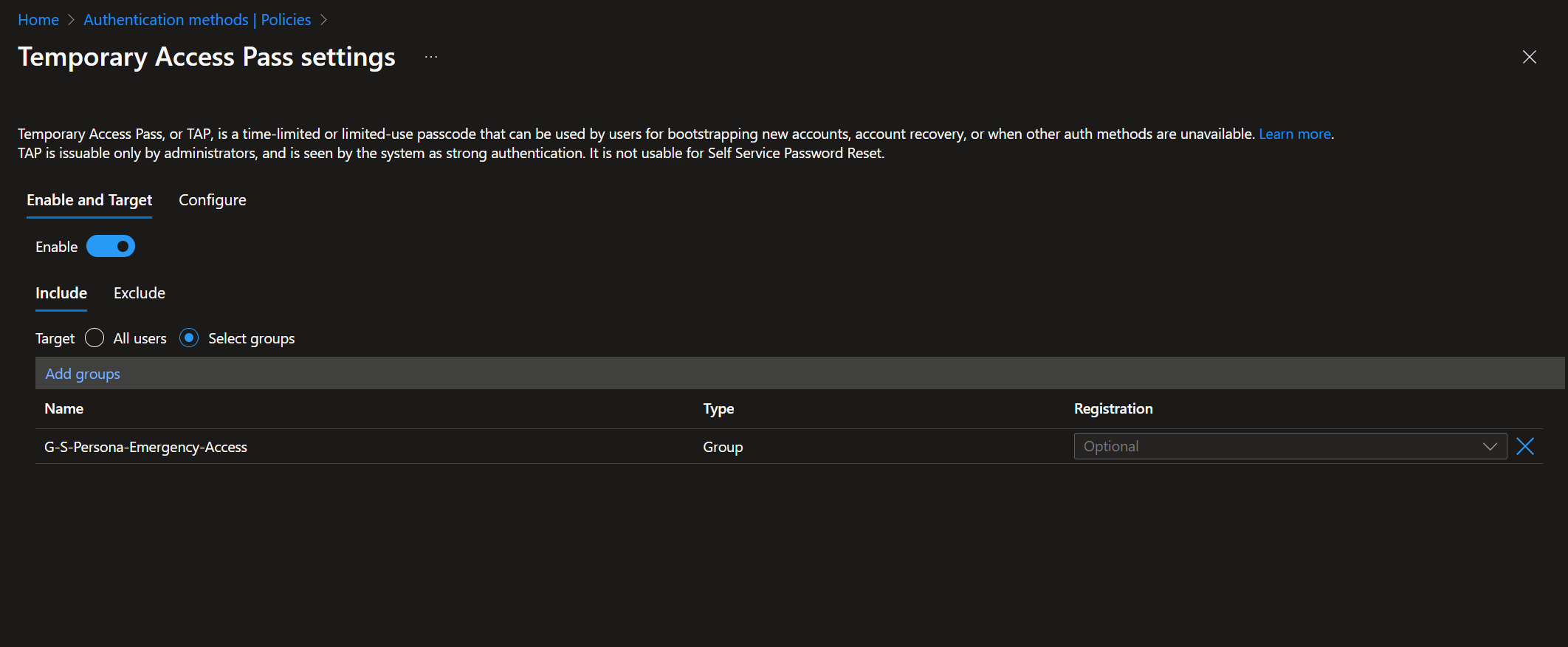
Generate a Temporary Access Pass
- In EntraID, navigate to the user of the emergency access account.
- Under the Manage blade, open the Authentication methods.
- Add an authentication method.
- Choose the method "Temporary Access Pass." Adjust the duration if needed and add it.
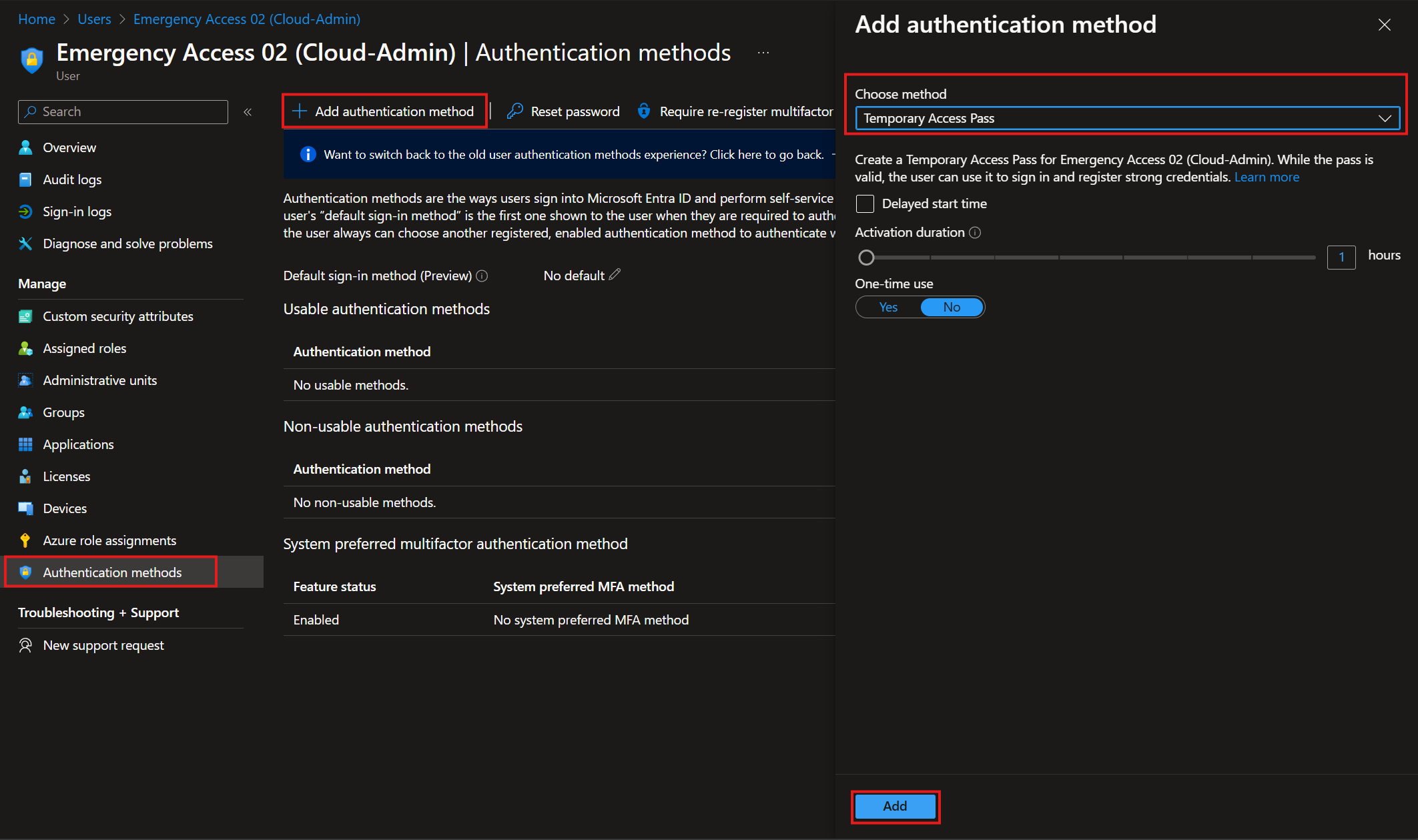
- Capture the temporary access pass (it will not be displayed again).
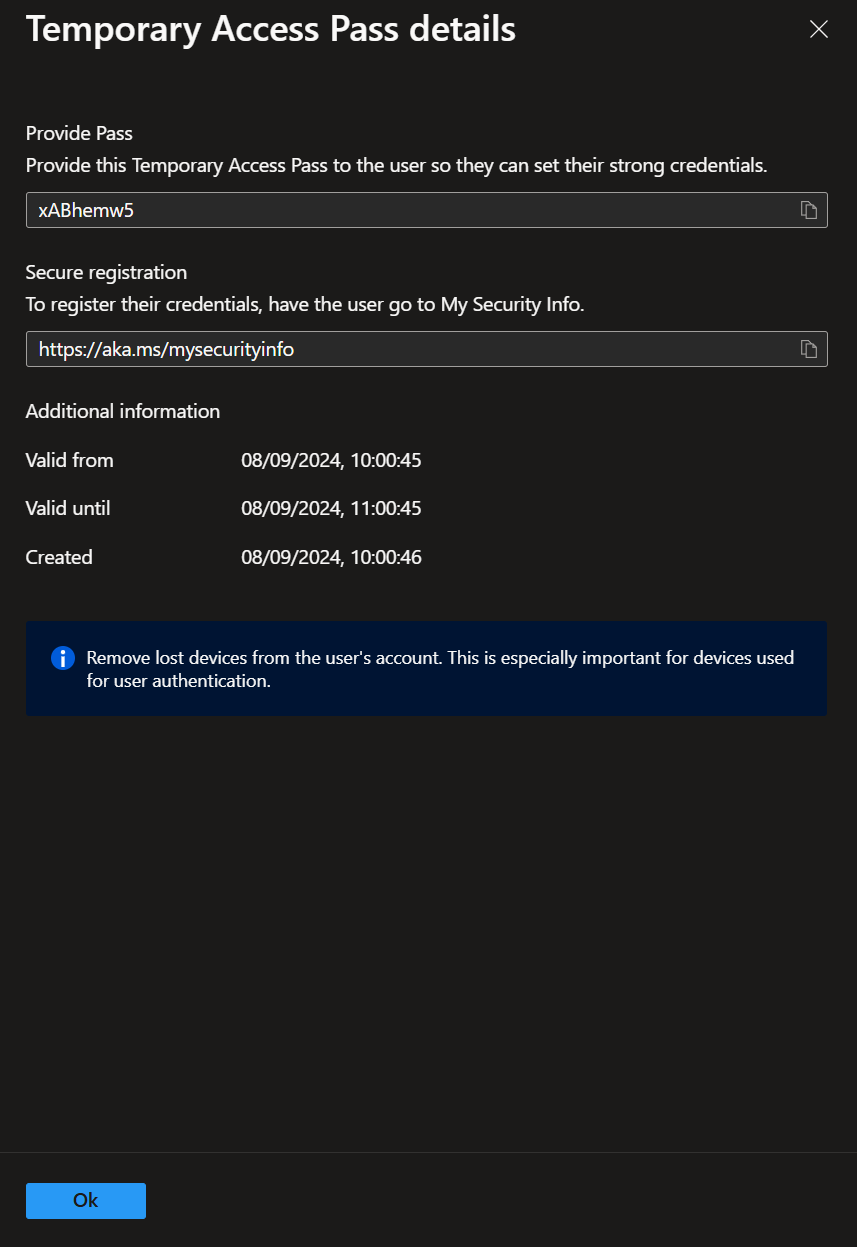
If your user interface appears different, you may need to activate the new user authentication methods experience.
Registering a FIDO2 Passkey
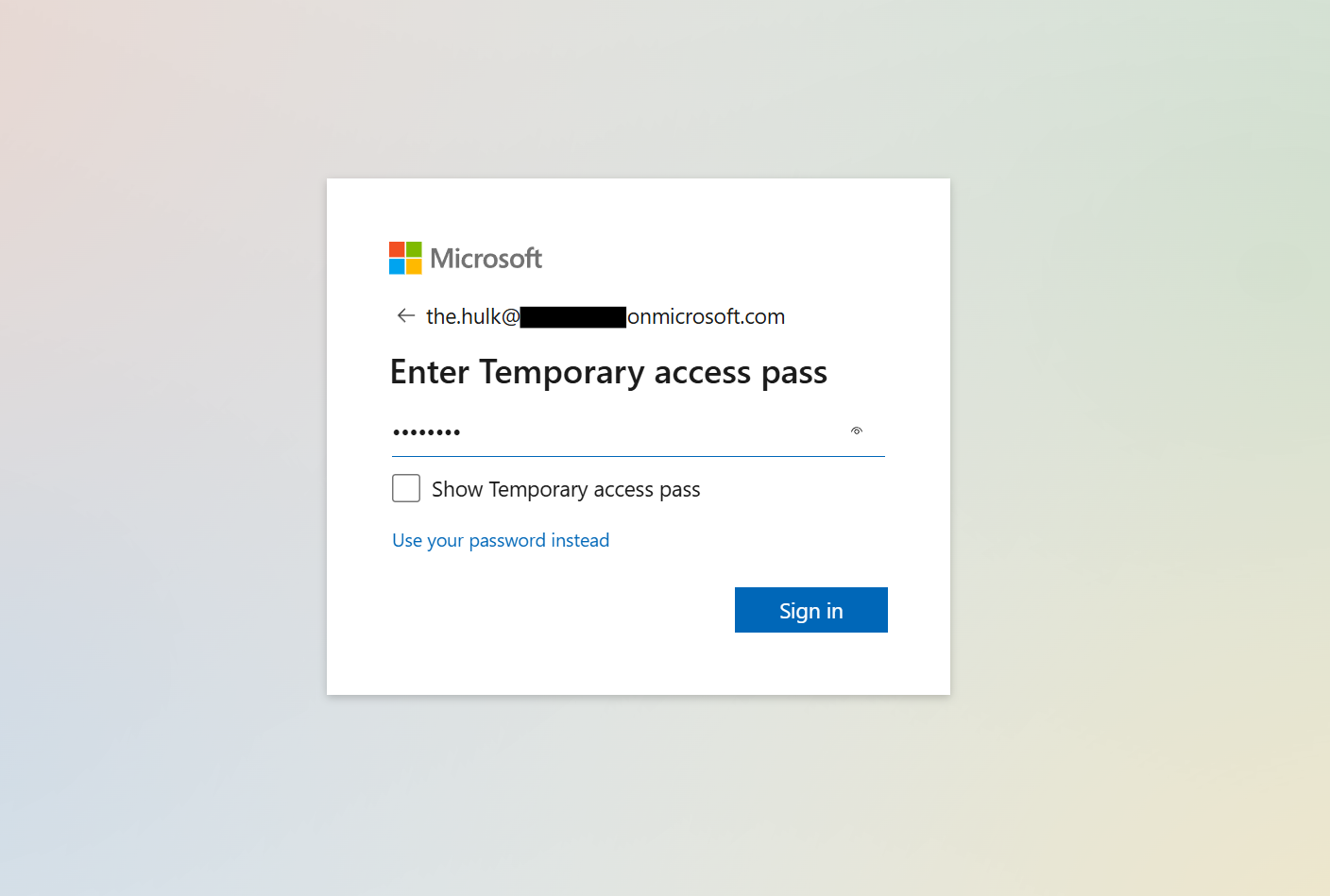
- Navigate to My Security Info.
- Log in using the temporary access pass.
- Add a FIDO2 Passkey.
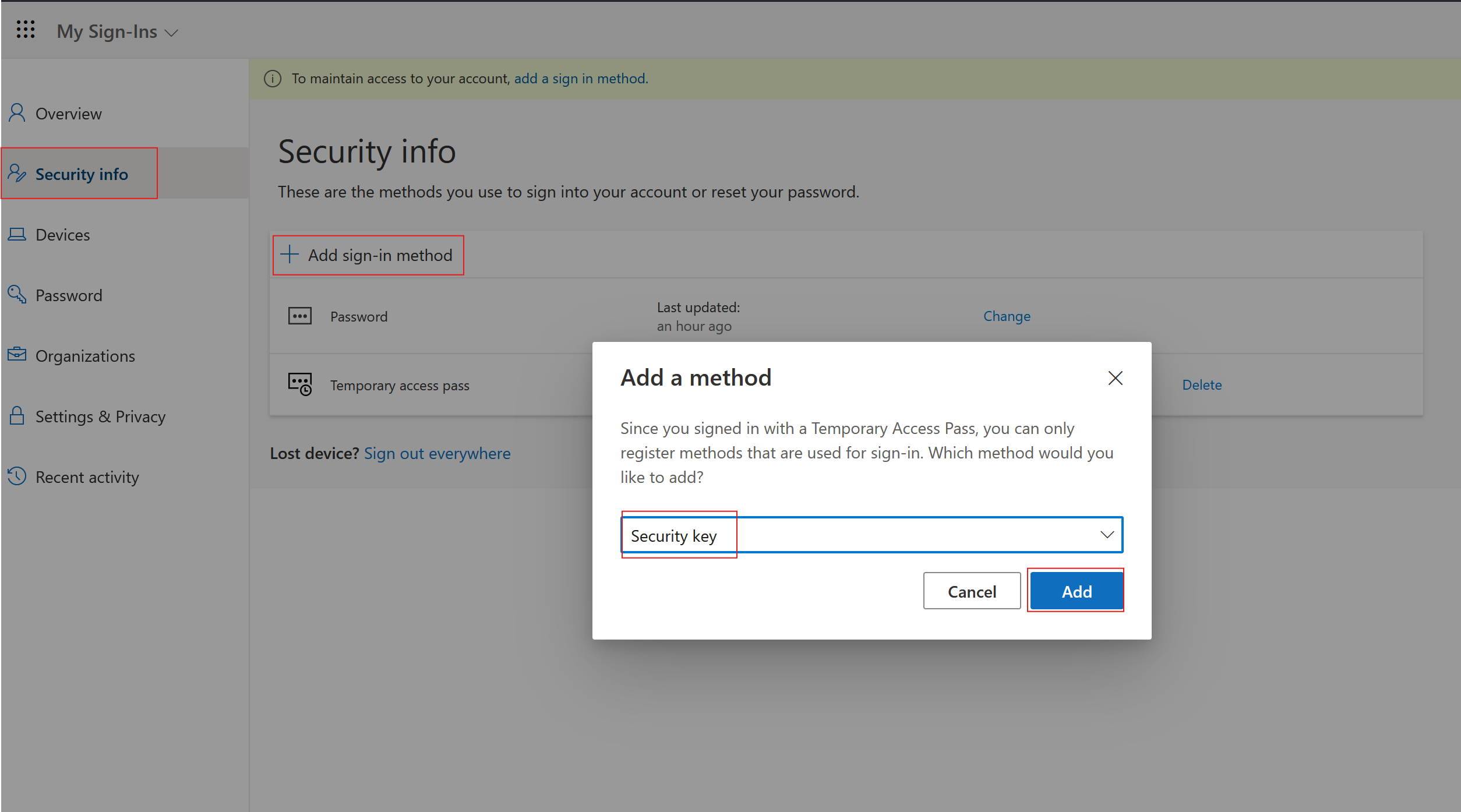
- If using a USB key, select that option.
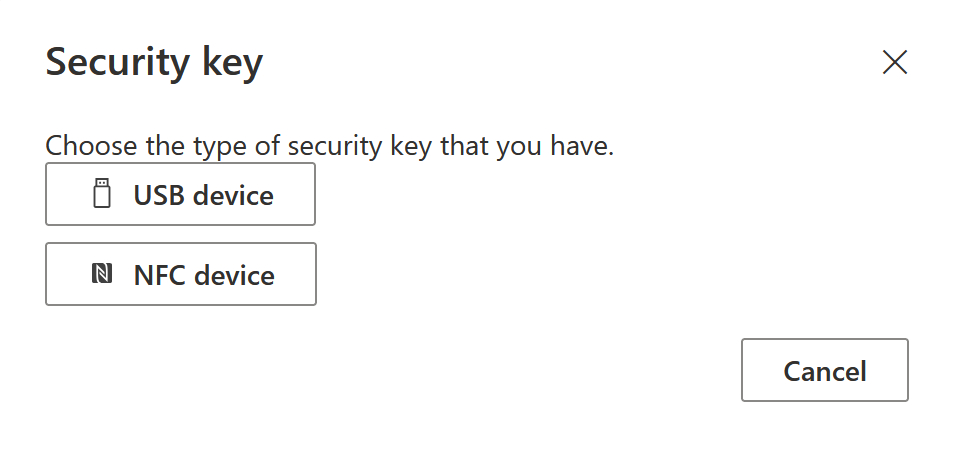
- After selecting USB, you will be redirected to a new window where you will be prompted to plug in your USB FIDO2 passkey and touch the button on the device itself.

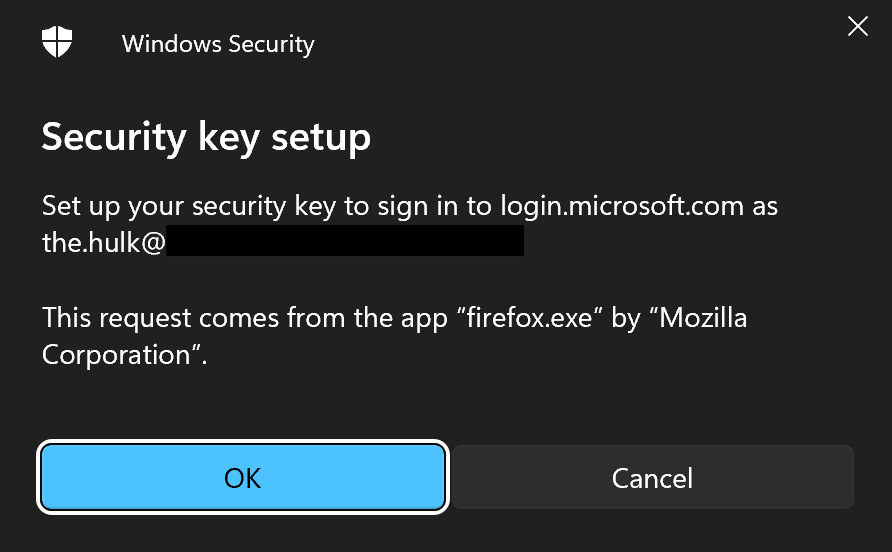
You should get this notice.
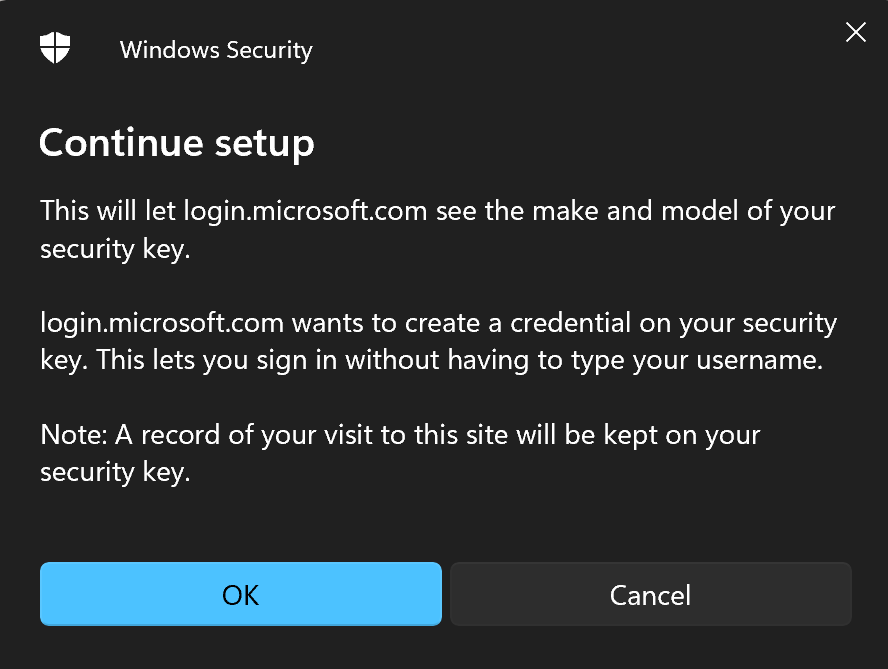
- Finally, you will be prompted to touch your security key.
Note: If your key is new, as mine is, you will first need to set up a new PIN for your key. In the future, you will be asked to enter the PIN to use the security key, so keep it safe (offline). - Finish setting up the new authentication method by logging in with it.
- Delete the Temporary Access Pass since it will no longer be needed.
- Repeat this process for any other emergency accounts you wish to establish.
Final Thoughts
FIDO2 keys are phishing-resistant and currently considered one of the safest authentication methods. They work well for tenants on Security Defaults and for tenants with at least a P1 license using Conditional Access policies.
Keep in mind that you should not mix these keys when using them for emergency access. The purpose of having multiple accounts is to avoid a single point of failure. Using one key for several accounts would undermine that objective.
Lastly, don't forget to set up monitoring for these accounts. At the very least, establish processes to periodically check the status of the accounts. It's crucial to be alerted if someone accidentally erases or modifies the authentication methods for these types of accounts. I will explore setting up monitoring in more detail in a future post.